
Web Services Security (WSS): SOAP Message Security is a set of enhancements to SOAP messaging that provides message integrity and confidentiality. WSS: SOAP Message Security is extensible, and can accommodate a variety of security models and encryption technologies.
WSS: SOAP Message Security provides three main mechanisms that can be used independently or together:
- The ability to send security tokens as part of a message, and for associating the security tokens with message content
- The ability to protect the contents of a message from unauthorized and undetected modification (message integrity)
- The ability to protect the contents of a message from unauthorized disclosure (message confidentiality).
WSS: SOAP Message Security can be used in conjunction with other web service extensions and application-specific protocols to satisfy a variety of security requirements.
In this article we will learn how to use different authentication options in SOAP UI. I’ll be using examples from test project on Parasoft site.
SOAPUI Testing with No Authentication
Create New Project in SOAPUI and by using WSDL Path: http://parabank.parasoft.com/parabank/services/store-01V2?wsdl
Now just open getItemByTitle operation and set title as Java and run the service.
In this service we not applied any authentication. These APIs are public and anyone can use.
SOAPUI Testing with UserName/Password Authentication
Create New Project in SOAPUI and by using WSDL Path:
http://parabank.parasoft.com/parabank/services/store-wss-01?wsdl
Now try same getItemByTitle as above and run it. It will show error message: An error was discovered processing the <wsse:Security> header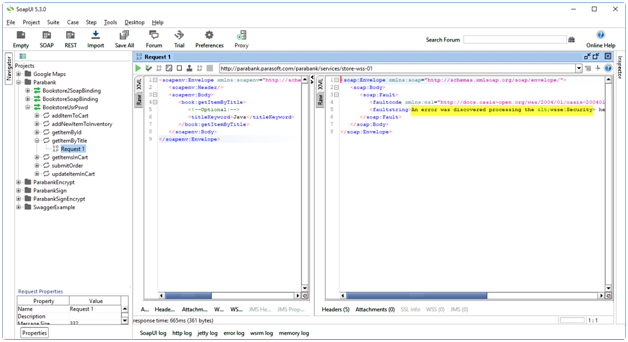
SoapUI manages WS-Security related configurations at the project level. If you click on the WS-Security Configurations tab on the project level you’ll find four sub tabs:
- Outgoing WS-Security Configurations: configurations that should be applied to outgoing messages, including requests and MockResponses. This configuration type is used for encryption, signing and adding SAML, timestamp and username headers.
- Incoming WS-Security Configurations: configurations that should be applied to incoming messages, including responses, MockRequests or monitored requests and responses. This configuration type is used for decrypting and verifying the signature of incoming messages.
- Keystores: keystores used for encryption, decryption and signing.
- Truststores: truststores used for signature verification.
Now double click on Project and switch to WS-Security Configuration tab. This will WS-Security configuration window. Switch to Outgoing WS-Security Configurations tab.
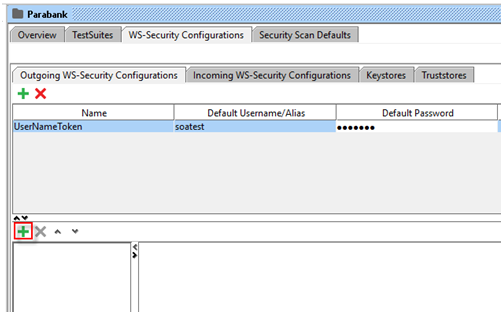
- Create a new outgoing configuration by clicking on the add button.

- Enter name of Outgoing Configuration

- Update Default Username/Alias and Default Password. Enter “soatest” for both.
- Now create a new Outgoing configurations entry by clicking on the lower add button.
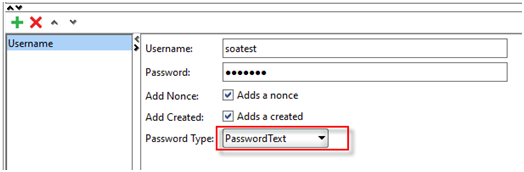
- Add User name

- Update Username and Password as “soatest”. Keep Add and Nonce and Add Created checkbox checked. Select PasswordText in Password Type drop down.
- Now Add outgoing configuration explicitly:-
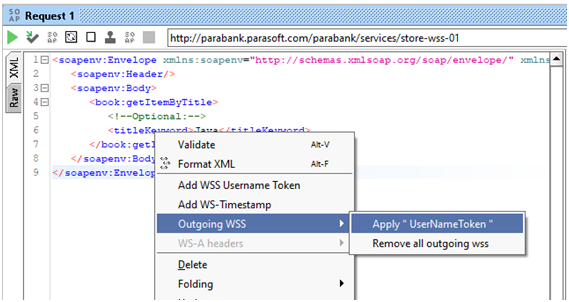
- And now run the request. This time it will show the successful result for books with title including java.
- If don’t want to apply outgoing WSS every time manually, use implicit option.
- Adding Configuration implicitly:-
- Use Auth option at bottom of request window
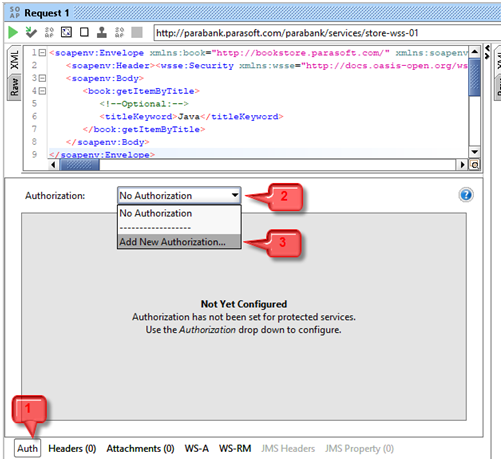
- Now select Basic type authorization and in choose Outgoing WSS you created above.
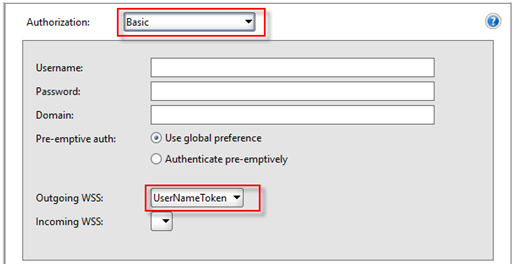
- You can click again on Auth tab at bottom of window to minimize the auth window.
- Use Auth option at bottom of request window
- Now you just run the request without adding Outgoing WSS configuration manually.
SOAPUI Testing with Signature WS-Security
Create New Project in SOAPUI and by using WSDL Path: http://parabank.parasoft.com/parabank/services/store-wss-02?wsdl
For this project clients need to sign the SOAP Body using the key store soatest.pfx.
key store password: security
certificate alias: soatest
private key alias: soatest
algorithm: RSA
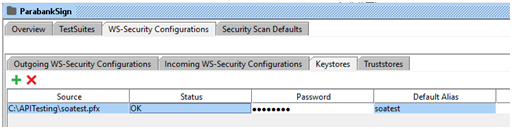
- Double click on Project and switch to WS-Security Configuration tab. This will WS-Security configuration window. Switch to Keystore tab.
- Add a keystore by clicking the add button and browsing to your keystore file.

- Enter the password for the keystore.

- Make sure that the Status is OK. If not, check your password and Status for errors. Update Default Alias and password.
- Create a new Outgoing configurations entry by clicking on the lower add button and update Default Username/Alias & Default Password.
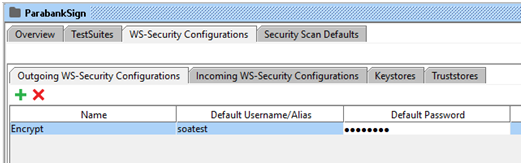
- Now add WSS entry and select Signature in drop-down
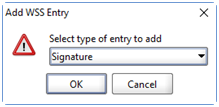
- User different options as per information provided by the API Development team

- Now save the WSS configuration and run the request by applying authorization explicitly or implicitly as described above.
SOAPUI Testing with Encryption WS-Security
Create New Project in SOAPUI and by using WSDL Path: http://parabank.parasoft.com/parabank/services/store-wss-03?wsdl
For this project clients need to sign the SOAP Body using the key store soatest.pfx.
key store password: security
public key alias: soatest
Responses have the SOAP Body encrypted using the same key.
- Double click on Project and switch to WS-Security Configuration tab. This will WS-Security configuration window. Switch to Keystore tab.
- Add a keystore by clicking the add button and browsing to your keystore file. Switch to Outgoing WS-Security configuration tab.
- Create a new Outgoing configurations entry by clicking on the lower add button and update Default Username/Alias & Default Password.
- Now add WSS entry and select Encryption in drop-down
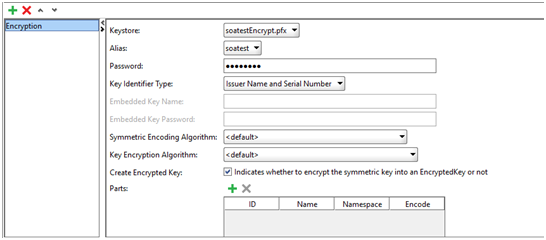
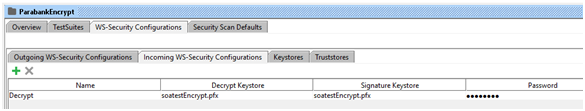
- Above steps are for request encryption. Incase response is encrypted then we need decryption wss as well to apply on incoming messages. So switch to Incoming WS-Security Configguration tab and add incoming WSS. Give a significant name and use provide password.
- Now apply outgoing and incoming wss in Auth tab.
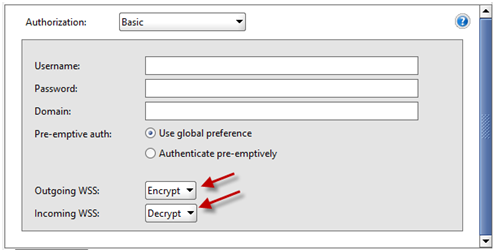
- Now hit the request and see the decrypted response.
- If hit the error refer – http://www.ourhints.com/java/error-while-decryption-of-soapui-response-error-getting-response-null/
SOAPUI Testing with Signature and Encryption WS-Security
Create New Project in SOAPUI and by using WSDL Path: http://parabank.parasoft.com/parabank/services/store-wss-04?wsdl
For this project clients need to sign the SOAP Body using the key store soatest.pfx.
key store password: security
key alias: soatest
Responses have the SOAP Body signed, then encrypted using the same key
- If both signature and encryption needs to be applied then same needs to be configured. Double click on Project and switch to WS-Security Configuration tab. This will WS-Security configuration window. Switch to Keystore tab.
- Add a keystore by clicking the add button and browsing to your keystore file. Switch to Outgoing WS-Security configuration tab.
- Create a new Outgoing configurations entry by clicking on the lower add button and update Default Username/Alias & Default Password.
- Now tricky part. Now add WSS entry and select Signature in dropdown. Follow steps explained in signature section and then again add another WSS entry and select encryption in dropdown. Follow steps explained in encryption section.
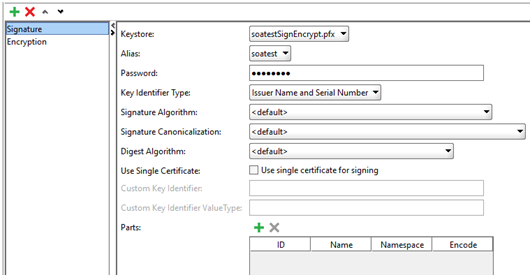
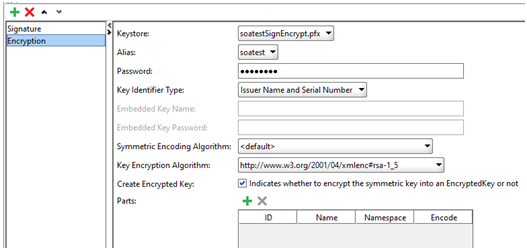
- Switch to Incoming WS-Security Configuration tab and created incoming wss.
- In Auth tab of request section apply both outgoing and incoming WSS.
- Hit the request and get the decrypted response.
- If hit error while decryption refer another article – Error while decryption of SOAPUI response- “Error Getting Response :null”
When I try to appy “SOAPUI Testing with Signature and Encryption WS-Security”, I get “An error was discovered processing the <wsse:Security> header” as response. What can be the problem?
Sorry for late reply. Please share more details of the error with all steps performed. Please check the SoapUI Log and error log and share here.
Hello,
I sent request and response messages to https://0bin.net/paste/e+PYMmz6uxrJOjhZ#4JUsazsOdnUyNG55pA09RNzdAhuXS9YrcKNb5JQUALj
SoapUI log is as below:
Wed Feb 20 08:03:02 EET 2019:DEBUG:Stale connection check
Wed Feb 20 08:03:02 EET 2019:DEBUG:Attempt 1 to execute request
Wed Feb 20 08:03:02 EET 2019:DEBUG:Sending request: POST /parabank/services/store-wss-04 HTTP/1.1
Wed Feb 20 08:03:03 EET 2019:DEBUG:Receiving response: HTTP/1.1 500
Wed Feb 20 08:03:03 EET 2019:DEBUG:Connection can be kept alive indefinitely
Wed Feb 20 08:03:03 EET 2019:INFO:Got response for [BookstoreSoapBinding.getItemById:Request 1] in 434ms (361 bytes)